What cybersecurity risks do maintenance and reliability teams face—and what can they do about it?
Know thy enemy. This has never been truer than in the field of cybersecurity, right now. With ransomware attacks escalating by the day, maintenance and reliability teams at critical facilities, government organizations, and manufacturers all need to assess their level of cyber risk and improve their cyber preventive maintenance actions. To help frame that task, cybersecurity expert Matthew Hudon and certified maintenance and reliability professional (CMRP) Frederic Boudart, both with Fluke Reliability, gave a webinar in June 2021 on “Managing cybersecurity risk in maintenance and reliability.”
“It’s not a question of if, it’s a question of when,” says Hudon. “A cybersecurity incident is going to happen to everyone at some point. The real question is, what level of disaster will it be and how long will it take you to recover?”
A good cyber preventive maintenance strategy will reduce risk, lower the severity of incidents, and increase the availability of core systems.
“So, how do you bring cybersecurity into maintenance?” asks Baudart. He advises teams to start by understanding the basic terminology and their relevance to your organization and then build a list of critical factors for your industry. That will inform your next steps.
Understanding cybersecurity for maintenance and reliability
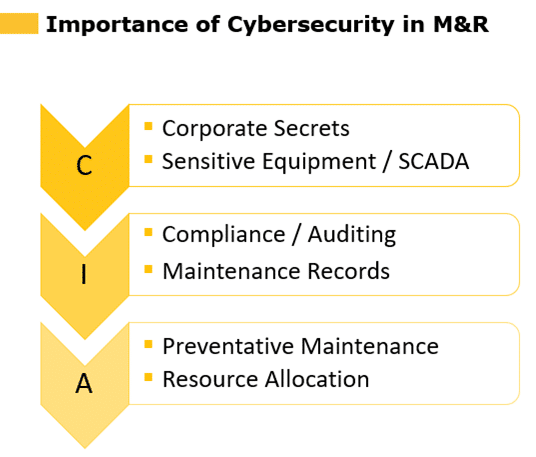
As Hudon demonstrates in Figure 1, the three most important facets of cybersecurity for maintenance and reliability are confidentiality, integrity, and availability.
- Confidentiality: Only appropriate people should have permission to access your data and information. The more sensitive the data, the fewer the number of people who should have access to limit potential breach points.
- Suggestion: Take a close look at access levels to data that qualifies as a corporate secret or that grants control over sensitive equipment, such as the SCADA system.
- Suggestion: Take a close look at access levels to data that qualifies as a corporate secret or that grants control over sensitive equipment, such as the SCADA system.
- Integrity: The data in your systems—from computerized maintenance management systems (CMMS) to supervisory control and data acquisition (SCADA) control systems—needs to be accurate. Operations and compliance both depend on accurate data; if it becomes corrupted, how far does the impact spread?
- Suggestion: Assess current data accuracy levels in your core systems and conduct an audit if necessary. What level of confidence do you have in your maintenance records and where are the vulnerable points in the process?
- Suggestion: Assess current data accuracy levels in your core systems and conduct an audit if necessary. What level of confidence do you have in your maintenance records and where are the vulnerable points in the process?
- Availability: What is the uptime quotient of your enterprise asset management (EAM) and other critical systems? Maintenance data must be available when needed. It’s essential to protect your maintenance systems from compromise for them to serve as the lynchpin to your organization.
- Suggestion: Apply preventive maintenance best practices to the IT infrastructure supporting your processes. Ask what needs to be done to maintain availability and regularly schedule any necessary downtime to run patches and “harden” the system (reduce the number of external entry points).
“There’s no point in using IoT or SAAS or any kind of information system at all if it’s not confidential, accurate, and available,” says Hudon. “Organizing your cybersecurity thinking around the three CIA principles is the first step for any maintenance organization.”
Critical cybersecurity factors
Hudon and Baudart drilled down into the specific risks and advisories for government, healthcare, and manufacturing, highlighting which aspects were common across the board and which merited special focus by industry.
Here are some of the common cybersecurity trends and considerations in maintenance departments, across industries:
- Restricting out-of-network devices. “There had been a general practice that, if IT didn’t want an IoT device on the network that we could get a hotspot and create a way for it to communicate outside the network,” says Baudart. “But now, we’re saying that’s not OK. Not only do we need to make sure that device has security controls in place, but we also want it on our network to make sure we’re maintaining compliance and governance over that information.”
- Vendor screening. For due diligence screening, have device vendors engage with IT early in the purchase consideration process. In addition to security factors, IT can also help verify that the product performs as promoted.
- Data sensitivity. Consider the risks associated with maintenance system data. For example, access to asset vibration trends probably would not cause concern, but access to process valve controls would.
- Compliance. While the specifics vary by industry, compliance requirements must be factored into any IIoT or other maintenance technology solution.
- Bandwidth. Does the network have the bandwidth to support a new device? How about 20, 30, 40, or 50 additional IoT sensors?
- Training. The most important training you can do is to teach people how to recognize phishing, whether by email or phone call. Don’t click on links, even when they look trustworthy and personalized.
So, how do people get anything accomplished with all of these requirements? “Getting things done is important, but so is taking the time to be secure,” Baudart says. “If you do your due diligence, then there shouldn’t be a problem. If you don’t, people may lose their jobs. Do you really want to take the chance?”
Here are some specific considerations across various industries:
- Government agencies must guarantee the confidentiality of the information on their systems and comply with the NIST 800-53 cybersecurity framework.
- Cautions:
- Do not assume that SaaS solutions are inherently secure; all IT solutions should be reviewed.
- Suggestions:
- Encrypt all data
- Implement a Governance, Risk, and Compliance (GCR) solution
- Cautions:
- Healthcare organizations should carefully consider the type of data source during the vendor selection process. Bluetooth vs. Ethernet carries different risks, and IoT devices that utilize a non-approved communication method will not be allowed.
- Cautions:
- Cloud-based CMMS systems may not be allowed; consider an on-prem or private-network implementation that allows for more local control.
- Suggestions:
- Utilize a detailed vendor questionnaire to flesh out IT requirements, supported protocols, and exceptions.
- Require VP approval for all IoT projects, to ensure workarounds do not escape review.
- Cautions:
- Manufacturing environments with sensitive SCADA systems may need to take extra precautions; compliance with NIST 171 / DFRAS often presents extra complications.
- Cautions:
- Schedule enough downtime to apply patches
- Suggestions:
- Encrypt all data
- Segregate networks
- Implement business continuity and disaster recovery program for your data
- Have a dedicated compliance and security person
- Cautions:
To overcome resistance within the team around prioritizing cybersecurity, Baudart says that the more assistance maintenance people receive from IT, the less resistance they tend to have. Learning what’s involved in cybersecurity compliance creates an understanding of what’s important and why. “Establish a relationship and things will become easier over time,” he says.
Checklist for IIoT and Cybersecurity considerations
- Equipment
Evaluate your existing assets, including software, hardware, data collection, analytics tools, and processes.
- Communications & Protocols
After you’ve developed a sense of what devices are included in your system, you’ll need to consider how to configure those devices and how they’ll communicate with each other. Communication must be both consistent and secure.
- Environment
Next, you’ll want to assess your environment. You’ll need to consider everything from the location itself to any potential issues, equipment, and installation logistics.
- Security
How will you protect sensitive data?
“It’s really important for anyone who works in operations and maintenance to understand the sensitivity of the data under their care,” says Hudon. “Too many times people may be inclined to say, ‘it’s just a temperature sensor,’ but that doesn’t make it unimportant for facility security.”
Above all, work closely with your IT department. “They want to help you,” says Baudart, “they are here to protect us.” For more detailed advice on cybersecurity for maintenance, watch the full webinar online.






